- The idea of a cipher system is to disguise information in such a way that its meaning is unintelligible to an unauthorized person.
- The two most common uses are, probably, to store data securely in a computer file or to transmit it across an insecure channel such as the internet.
- Encrypted document does not prevent unauthorized people gaining access to it but, rather, ensures that they cannot understand what they see.
- plaintext - original messageciphertext - coded messagecipher - algorithm for transforming plaintext to ciphertext
- key - info used in cipher known only to sender/receiver
- encipher (encrypt) - converting plaintext to ciphertext
- decipher (decrypt) - recovering ciphertext from plaintext
- cryptography - study of encryption principles/methods
- cryptanalysis (codebreaking) - study of principles/ methods of deciphering ciphertext without knowing key
- cryptology - field of both cryptography and cryptanalysis
- Classified along three independent dimensions:
- The type of operations used for transforming plaintext to ciphertext
- The number of keys used
- symmetric (single key, or private-key encryption)
- asymmetric (two-keys, or public-key encryption)
- The way in which the plaintext is processed


Symmetric Cryptography Principles
Symmetric vs. Asymmetric
One of the most difficult aspects of obtaining a secure system.
However it is then replaced by the problem of guaranteeing the authenticity of each participant’s encryption key.
Methods use in Cryptography Algorithm
Substitution
monoalphabetic substitution
Formed by shifting the letters of the original alphabet
polyalphabetic substitution
Extension of monoalphabetic substitution system
Using Vigenere Tableau
Transposition
unkeyed transposition
Rearrange letters by using matrix
keyed transposition
Rearrange letters by using matrix where the size of matrix is determined by the length of the key used.
Caesar Ciphers
In this cipher each of the letters A to W is encrypted by being represented by the letter that occurs three places after it in the alphabet.
Although Caesar used a ‘shift’ of 3, a similar effect could have been achieve using any number from 1 to 25.
1. In fact any shift is now commonly regarded as defining a Caesar Cipher.
The encryption key and decryption key are both determined by a shift but the encryption and decryption rules are different.
We could have changed the formulation slightly to make the two rules coincide and have different encryption and decryption keys.
A shift of 26 has the same effect as a shift of 0 and, for any shift from 0 to 25, encryption with that shift is the same as decryption with the new shift obtained by subtracting the original shift from 26.
E.g: encryption with shift 8 is the same as decryption with shift 26 - 8 =18.
This enable us to use the same rule for encryption and decryption with the decryption key 18 corresponding to the encryption key 8.
Caesar ciphers are vulnerable to exhaustive key search attack.
To work through all the 26 keys.
Furthermore the key can be determined from knowledge of a single pair of corresponding plaintext and ciphertext characters.
Vigenère Ciphers
The Vigenère cipher is a method of encrypting alphabetic text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution.
This cipher is well known because while it is easy to understand and implement, it often appears to beginners to be unbreakable; this earned it the description le chiffre indéchiffrable (French for 'the unbreakable cipher'). Consequently, many people have tried to implement encryption schemes that are essentially Vigenère ciphers, only to have them broken.
The left-hand (key) column of this square contains the English alphabet and for each letter, the row determined by that letter contains a rotation of the alphabet with that letter as the leading character.
So each letter in the left-hand column gives a Caesar Cipher whose shift is determined by that letter.
Example: the letter g gives the Caesar Cipher with shift 6.
Vigenere Table
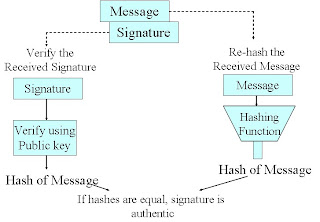
Digital signature
Hash Function
How to Create a Digital Signature Using RSA
How to Verify a Digital Signature Using RSA
SUMMARY
have considered:
Authentication concepts and techniques
Cryptography concept and techniques
principles of private and public-key cryptography
RSA algorithm, implementation, security
Methods of attack in Digital Signature, Encryption and RSA
END OF LECTURE 2
Review Questions - Lab 2
1. What file system is compatible by Windows 2003?
- NTFS (NT File System).
2. What is the default permission when a partition is formatted with NTFS?
- Full Control: Enables a user to view or change a folder’s attributes, permissions and take ownership. A user is also able to create, modify and delete folders. Users can also traverse folders and execute files that contain programs stored in a folder. The Full Control permissions allow users to compress files as well.
- Read and Execute: The rights enabled by this permission include traversing folders and executing files in the folders, listing a folder’s content, and viewing the attributes of folders.
- Write: Users are able to create new folders, new subfolders and new files in the folders. A user is also able to change a folder’s attributes.
- List Folder Contents: Users are able to transverse folders, list the contents of the folder, and view a folder’s attributes.
- Modify: A user can change the properties of a folder, create new folders, and also delete folders.
- Read: This permission enables a user to view the folder, and any subfolders and files stored within the folder.
3. Who has access to the volume when a partition is formatted with NTFS?
- In order to maintain access control on files and folders and support limited accounts, you must use NTFS. If you use FAT32, all users will have access to all files on your hard drive, regardless of their account type (administrator, limited, or standard.)
- A computer running Windows XP or Windows 2000 can access files on an NTFS partition. A computer running Windows NT 4.0 with Service Pack 4 or later might be able to access some files. Other operating systems allow no access.
4. What is the best way to secure files and folders that you share on NTFS partitions?
- The best way that you can do to secure files and folders that you share on NTFS partitions is first you can create two account which is the first account as the admin that only can log on by the authorized person only that have rights on the files or folders and the other account can be unlimited user which is they cannot access the files and folders.
Make sure the admin account have the password.
5. What is the definition of data confidentiality?
- Data that is secured so only the intended people have access.
6. If a user has Write permission for a folder and is also a member of a group with Read permission for the folder, what are the user's effective permissions for the folder?
- All the members in that group only have the permission for read the folder only.
- They can’t changes the contain of the data in the folder
7. What is the best way to define the data availability?
- Data that can be accessed when it is needed.
8. How the data confidentiality affect data availability?
- Data that is secured too weakly may conflict with the availability.
9. List two technologies can be used to help reduce downtime and increase the time data is readily available.
- clustering
- load balancing
10. What is the definition of data integrity?
- Data that has not been tampered with intentionally or accidentally.
11. List two threats that can be used to damage the data integrity.
- virus
- hacker
- worm
12. Data integrity can also be threatened by environmental hazards such as dust, surges and excessive heat. True or False?
- True






Brilliant post. In this article a complete overview of this security technique is explained. The review questions helped me to check my understanding. Thanks for this great write up.
ReplyDeleteeSignature